Everyday is a chance to do good. Or in the case of phishers, to do evil.
Today, ITS detected a phishing email campaign aimed at the Manhattan College community. The phishing email claims to be from the college's "Manhattan Mail Delivery Subsystem." It requests the user to click a phishing link (that displays a manhattan.edu URL but actually directs to an absolutely different domain), login with their credentials and review undelivered email messages.
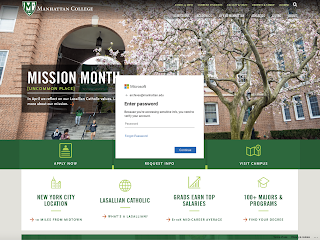 |
| Phishing login webpage that is aimed at the Manhattan College community. |
Everyday the college receives phishing campaigns. This particular campaign is notable due to the branding of the phishing login webpage. Notice the differences between this phishing login webpage and the official login webpage that you typically use. Now consider that the phishers could copy the official login webpage's design.
ITS asks you to be mindful of the URL shown in your browser's location bar when you are prompted for your credentials. This will help us to be less vulnerable to such attacks. Also when you see a link be mindful that the text displayed is not necessarily the URL address used (e.g.,
http://www.google.com).
You may ask, what should be asked of ITS though. First, ITS (along with our email service) attempts to prevent phishing emails from being delivered successfully. If the phishing emails have been delivered successfully, the phishing emails are quarantined (i.e., clawed away from inboxes, spam folders, etc.). Second, any recipient who interacted with the phishing email is notified and advised to change their password in the case that it was phished. Third, the hosting provider is notified of the abuse as is the sending email address' domain or the host of the sending email server. Lastly, we review our practices with respect to improving our response to future attacks.

