Gregory Quaglieni and Richard Musal will be presenting at March 27th in Providence Rhode Island at the Nercomp Regional Conference & May 10th in Miami Florida for the TeamDynamix Client Summit. Both presentations will be regarding how we got our Service Desk to be 90% Student Run.
Nercomp Prentation
TeamDynamix Presentation
Wednesday, December 20, 2017
Friday, December 15, 2017
COMPLETE: Planned Network Wireless Maintenance - Jan 11 at 7am
UPDATE2: As of 9:00am this morning, the planned network wireless maintenance was completed successfully. If you have any questions, please contact ITS via email at its@manhattan.edu or at extension x-7973.
UPDATE: Due to the campus closure and delayed opening on January 4th-5th, ITS was unable to do testing before we could conduct this wireless network migration on January 8th. This network migration will be rescheduled for this Thursday, January 11th from 7am-9am.
ITS will be conducting network maintenance on the wireless network in RLC, Leo, Memorial, Miguel, and DLS Halls. This scheduled maintenance will be conducted on January 8, 2018 from 7am to 9am.
In order to improve the wireless network reliability in these locations, there will be scheduled network maintenance in order to migrate the wireless networks. This scheduled network maintenance will affect only the wireless network in RLC, Leo, Memorial, Miguel, and DLS Halls. The wired networks in all buildings and the wireless networks on the rest of campus will not be affected.
We apologize for the inconvenience that this may cause. If you have any questions, please contact ITS at extension x-7973 or via email at its@manhattan.edu.
UPDATE: Due to the campus closure and delayed opening on January 4th-5th, ITS was unable to do testing before we could conduct this wireless network migration on January 8th. This network migration will be rescheduled for this Thursday, January 11th from 7am-9am.
ITS will be conducting network maintenance on the wireless network in RLC, Leo, Memorial, Miguel, and DLS Halls. This scheduled maintenance will be conducted on January 8, 2018 from 7am to 9am.
In order to improve the wireless network reliability in these locations, there will be scheduled network maintenance in order to migrate the wireless networks. This scheduled network maintenance will affect only the wireless network in RLC, Leo, Memorial, Miguel, and DLS Halls. The wired networks in all buildings and the wireless networks on the rest of campus will not be affected.
We apologize for the inconvenience that this may cause. If you have any questions, please contact ITS at extension x-7973 or via email at its@manhattan.edu.
COMPLETED: Dorm Wired Network Maintenance
UPDATE4: Overlook Manor was completed as of 11:30am today, Jan 8th. This wired maintentance is now complete. If you have any questions, please feel free to contact ITS at x-7973 or its@manhattan.edu
UPDATE3: Jasper Hall has been successfully completed as of 11:30am today.
UPDATE2: Chrysostom and Lee Halls have been successfully completed as of 12:30pm today.
UPDATE: Horan Hall was completed this morning. Lee Hall and Chrysostom will be completed tomorrow, December 20th.
ITS will be conducting network maintenance on the dorm wired networks throughout campus. This scheduled maintenance will be conducted from December 19th to January 5th, according to the schedule below, and will cause some localized wired network outages on a roaming basis in the dorms only. This will not affect other parts of the campus, nor will it affect Jaspernet wireless throughout the dorms.
In order to improve the dorm wired network reliability, there will be scheduled network maintenance in order to migrate the dorm wired networks. This network maintenance will affect the wired networks in all of the dorm buildings across campus. The dorm wired network maintenance schedule will be as follows:
We apologize for this inconvenience. If you have any questions, please feel free to contact ITS at x-7973 or its@manhattan.edu
UPDATE3: Jasper Hall has been successfully completed as of 11:30am today.
UPDATE2: Chrysostom and Lee Halls have been successfully completed as of 12:30pm today.
UPDATE: Horan Hall was completed this morning. Lee Hall and Chrysostom will be completed tomorrow, December 20th.
ITS will be conducting network maintenance on the dorm wired networks throughout campus. This scheduled maintenance will be conducted from December 19th to January 5th, according to the schedule below, and will cause some localized wired network outages on a roaming basis in the dorms only. This will not affect other parts of the campus, nor will it affect Jaspernet wireless throughout the dorms.
In order to improve the dorm wired network reliability, there will be scheduled network maintenance in order to migrate the dorm wired networks. This network maintenance will affect the wired networks in all of the dorm buildings across campus. The dorm wired network maintenance schedule will be as follows:
- Horan Hall and Lee Hall - Tuesday, December 19th
- Horan Hall will be first, followed by Lee Hall
- Chrysostom - Wednesday, December 20th
- Jasper Hall - Wednesday, January 3, 2018
- Overlook Manor - Thursday, January 4, 2018
We apologize for this inconvenience. If you have any questions, please feel free to contact ITS at x-7973 or its@manhattan.edu
Thursday, December 14, 2017
Operations Team Meets New Milestone
The Operations Team has reduced the average number of days to close tickets by one day. See details here.
Wednesday, December 13, 2017
COMPLETE: Horan Hall - Brief Network Outage 12/18 at 10am
UPDATE: As of 10:40 this morning, the generator test in Horan Hall has been successfully completed.
Physical Plant will be conducting a generator test in Horan Hall Monday, December 18th at approximately 10am.
There will be two brief outages, one while switching to generator power, the other while switching back to main power.
This will not affect the rest of campus.
Physical Plant will be conducting a generator test in Horan Hall Monday, December 18th at approximately 10am.
There will be two brief outages, one while switching to generator power, the other while switching back to main power.
This will not affect the rest of campus.
Monday, December 11, 2017
Reminder: Transition to Google Drive File Stream
Google Drive Sync ends support on December 11, 2017.
Drive File Stream is a new way to access all of your Google Drive files directly from your Mac or PC, without using up all your disk space. Unlike traditional file sync tools, Drive File Stream doesn’t require you to download your files first in order to access them from your computer. Instead, when you need to view or edit a file, it automatically streams from the cloud, on-demand. With Drive File Stream, your team will spend less time waiting for files to sync, no time worrying about disk space, and more time being productive.
With Drive File Stream, you can:
- Quickly see all your Google Drive files in Finder/Explorer (including Team Drives).
- Browse and organize Google Drive files without downloading all of them to your computer.
- Choose which files or folders you'd like to make available offline.
- Open files in common apps like Microsoft Office and Adobe Photoshop.
Note: This is only relevant for those that use a sync app such as Google Drive Sync. If you only use the web app (https://drive.google.com/) no action is required.
Environment
Windows
MacOSX
Google Drive
How do I get started?
Visit the Drive Help Center to install Drive File Stream and get started.
Solution:
Install Google Drive Stream. At the conclusion of the installation, you will get a pop up asking whether you want to replace Google Drive Sync with Drive Stream or whether you want to use both. It is recommended that you select "Yes" indicating that you wish to replace.
What about the current Drive application? Before installing File Stream, Google recommends removing the current Drive folder. For ease of use, we think it's best to uninstall the current Drive client.
Uninstall Drive and install File Stream
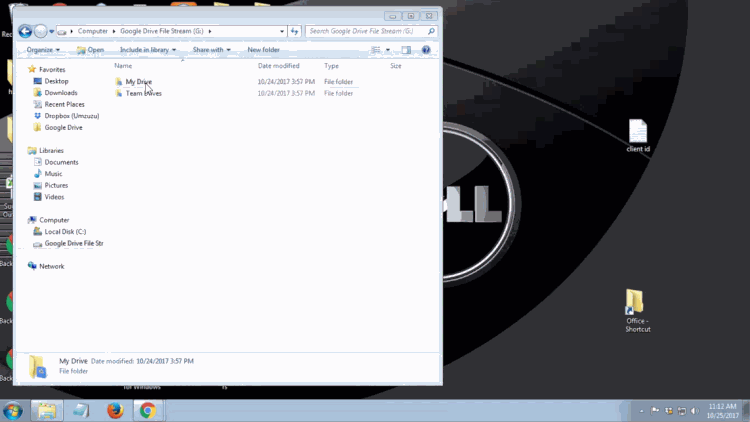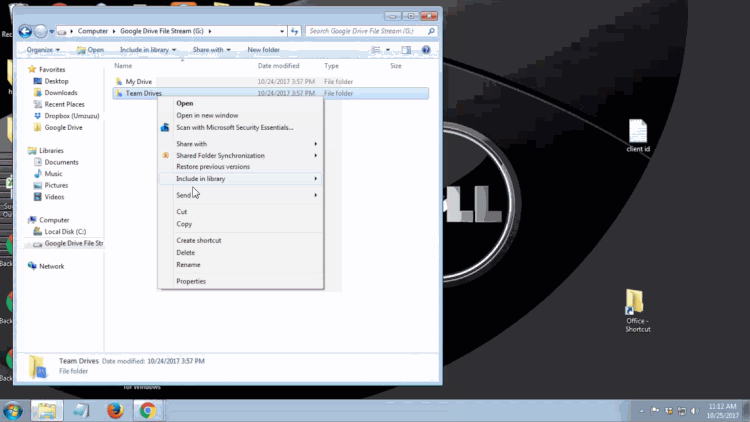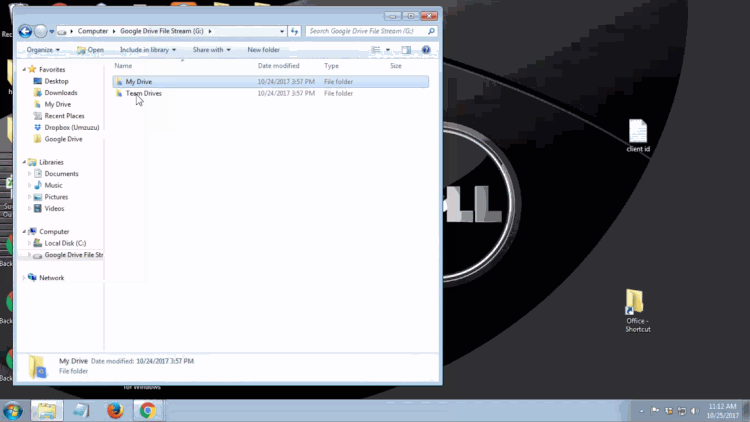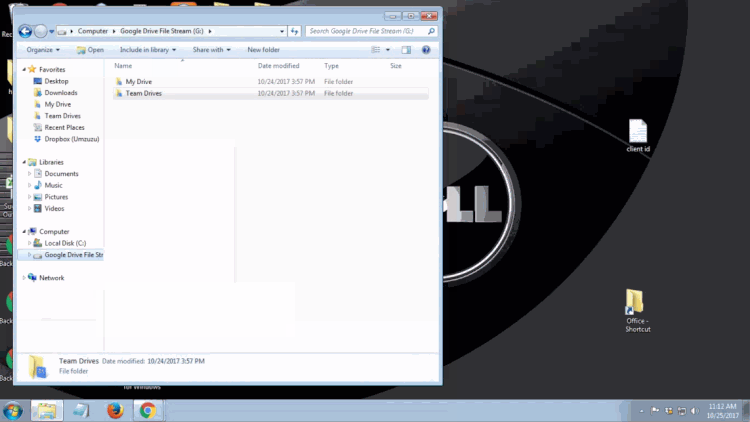
1. Uninstall the previous Google Drive app or Backup and Sync if it is present on your computer. To uninstall, navigate to the Windows icon in the bottom left corner of the screen and search for "Control Panel" and proceed to open it. You should be greeted with this window:
 Once you click on "Program and Features," you will be shown a list of programs that are installed on your computer. Navigate to the Google Drive app that you previously installed on your PC and select it. You will then see appear the option to uninstall that program. Proceed with the uninstall to completely remove the program from your PC.
Once you click on "Program and Features," you will be shown a list of programs that are installed on your computer. Navigate to the Google Drive app that you previously installed on your PC and select it. You will then see appear the option to uninstall that program. Proceed with the uninstall to completely remove the program from your PC.
2. Delete Google Drive Sync folder from your computer. It is a local folder only now and no longer syncs.
3. Install Drive File Stream. You can find it here. Depending on preferences of the User, it can be a good idea to create shortcuts on the desktop and in the Favorites or Quick Access areas of Windows and MacOS. We also recommend removing any shortcuts to the previous Google Drive folder to avoid confusion.
Also, the Drive File Stream icon in the Windows task bar will be grey, that should be the only Google Drive icon found in the task bar. If you see the older Google Drive Sync colored icon still on your computer go back to step 2 and delete old Google Drive Sync folder.
Friday, December 8, 2017
Classroom Technology Survey
Please take a few minutes to provide feedback on the latest generation Renovated Classroom. We will use this feedback when planning for future renovations.
Click here for the survey.
Click here for the survey.
Client Services Support Update - Finals Week Fall 2017
All of Client Services and Operations offices will be extremely short staffed between the hours of 7:30am-10:30am Monday through Friday during Fall 2017 Finals Week. This is due to the block scheduling and studying of finals going forward, and is out of ITS' control. The timeframe for each staff shortage will change each semester due to schedule changes made by scholastic department chairs.
Within this time frame, only the following types of issues will be addressed:
Major Outages
Classroom Emergency Issues
Previously Scheduled Appointments
All other requests will be processed in the order of which they were received. In addition, we will have a surge of staff members after 10:30am, to address immediate issues as they arise. Please be mindful this policy is being put into place so that we can better support the Manhattan College community.
If you have any specific questions or concerns, please email its@manhattan.edu or call 718-862-7973
Within this time frame, only the following types of issues will be addressed:
Major Outages
Classroom Emergency Issues
Previously Scheduled Appointments
All other requests will be processed in the order of which they were received. In addition, we will have a surge of staff members after 10:30am, to address immediate issues as they arise. Please be mindful this policy is being put into place so that we can better support the Manhattan College community.
If you have any specific questions or concerns, please email its@manhattan.edu or call 718-862-7973
Monday, December 4, 2017
Reminder: Transition to Google Drive File Stream
Google Drive Sync ends support on December 11, 2017.
Drive File Stream is a new way to access all of your Google Drive files directly from your Mac or PC, without using up all your disk space. Unlike traditional file sync tools, Drive File Stream doesn’t require you to download your files first in order to access them from your computer. Instead, when you need to view or edit a file, it automatically streams from the cloud, on-demand. With Drive File Stream, your team will spend less time waiting for files to sync, no time worrying about disk space, and more time being productive.
With Drive File Stream, you can:
- Quickly see all your Google Drive files in Finder/Explorer (including Team Drives).
- Browse and organize Google Drive files without downloading all of them to your computer.
- Choose which files or folders you'd like to make available offline.
- Open files in common apps like Microsoft Office and Adobe Photoshop.
Environment
Windows
MacOSX
Google Drive
How do I get started?
Visit the Drive Help Center to install Drive File Stream and get started.
Solution:
Install Google Drive Stream. At the conclusion of the installation, you will get a pop up asking whether you want to replace Google Drive Sync with Drive Stream or whether you want to use both. It is recommended that you select "Yes" indicating that you wish to replace.
What about the current Drive application? Before installing File Stream, Google recommends removing the current Drive folder. For ease of use, we think it's best to uninstall the current Drive client.
Uninstall Drive and install File Stream
1. Uninstall the previous Google Drive app or Backup and Sync if it is present on your computer. To uninstall, navigate to the Windows icon in the bottom left corner of the screen and search for "Control Panel" and proceed to open it. You should be greeted with this window:
 Once you click on "Program and Features," you will be shown a list of programs that are installed on your computer. Navigate to the Google Drive app that you previously installed on your PC and select it. You will then see appear the option to uninstall that program. Proceed with the uninstall to completely remove the program from your PC.
Once you click on "Program and Features," you will be shown a list of programs that are installed on your computer. Navigate to the Google Drive app that you previously installed on your PC and select it. You will then see appear the option to uninstall that program. Proceed with the uninstall to completely remove the program from your PC.
2. Delete Google Drive Sync folder from your computer. It is a local folder only now and no longer syncs.
3. Install Drive File Stream. You can find it here. Depending on preferences of the User, it can be a good idea to create shortcuts on the desktop and in the Favorites or Quick Access areas of Windows and MacOS. We also recommend removing any shortcuts to the previous Google Drive folder to avoid confusion.
Also, the Drive File Stream icon in the Windows task bar will be grey, that should be the only Google Drive icon found in the task bar. If you see the older Google Drive Sync colored icon still on your computer go back to step 2 and delete old Google Drive Sync folder.

Sunday, December 3, 2017
Mobile Devices Won't Secure Themselves!
Mobile security at one time meant using a laptop lock and keeping tabs on your phone. However, the growing capabilities and use of mobile devices — coupled with the ubiquity of smart devices stitched into the very fabric of our daily lives (figuratively and literally) — now require a more sophisticated defense-in-depth approach to match the growing threat. Following are a few things you can do to protect your devices and personal information on campus, at home, or at work.
- Secure your devices with a strong password, pattern, or biometric authentication. Check the settings for each device to enable a screen-lock option. For home routers, reset the default password with a strong one.
- Install anti-malware. Some software includes features that let you do automatic backups and track your device.
- Check your Bluetooth and GPS access. Disable these settings on all devices when not needed and avoid using them in public areas.
- Update your devices often. Install operating system and application updates when they become available.
- Review phone apps regularly. Remove any apps you don’t use. Be selective when buying or installing new apps. Install only those from trusted sources and avoid any that ask for unnecessary access to your personal information.
- Treat devices like cash! Don’t let your devices out of your sight or grasp. Maintain physical control of your device in public areas. Get a lock (alarmed is best) for your laptop and use it.
- Keep it sunny in the cloud. Whether using Google Drive, Dropbox, OneDrive, iCloud, Amazon Drive, or any of the many cloud options, set privacy restrictions on your files to share them only with those you intend. Protect access to your cloud drive with two-factor authentication.
- Create a secure wireless network. Configure your wireless router to protect your bandwidth, identifiable information, and personal computer. Secure it with proper set up and placement, router configuration, and a unique password, using the strongest encryption option. See http://www.wi-fi.org/ for more tips.
- Protect your Internet of Things (IoT) devices. Are you sharing your livestreaming nanny cam with the world? Review privacy settings for all Internet-ready devices before connecting them to the web.
Partially reposted from: https://er.educause.edu/blogs/2016/11/december-2017-your-mobile-devices-wont-secure-themselves
Friday, December 1, 2017
ITS Ticketing Survey Requests
In our continued efforts to gather feedback on the service we provide, we made a change to our ticketing survey system that sent out survey requests for previously resolved tickets. We were not aware that this change would cause this action and we do apologize for any confusion or inconvenience that it caused. This should not occur again. Thank you for your understanding.
LabSeat Outage Resolved
Update: We have identified a solution that is approved by LabStats. The Desktop Operations team is working on deploying it now. We expect that LabSeat data should be correct by Monday morning
At 7:22AM Friday December 1st, 2017 it was discovered that LabStats, the product powering LabSeat, is experiencing an outage. Manhattan College ITS immediately reported the issue to LabStats Support. We are awaiting an update from LabStats. This post will be updated when we receive communication from LabStats.
At 7:22AM Friday December 1st, 2017 it was discovered that LabStats, the product powering LabSeat, is experiencing an outage. Manhattan College ITS immediately reported the issue to LabStats Support. We are awaiting an update from LabStats. This post will be updated when we receive communication from LabStats.
Wednesday, November 29, 2017
Mac Users Take Note Take Immediate Action to Plug Security Hole
Update 2:52PM Thursday November 29, 2017:
Apple has released an update that fixes this vulnerability. Please update your Mac ASAP.
Here is the information regarding the update.
A security hole was recently discovered in the latest version of Mac OS X High Sierra which allows for anyone to access your computer without a password. We have provided a link to a USA Today article below, but there are many articles on the web reporting this issue. While Apple is working on a fix via update, you should take immediate action to fix the issue by following the instructions here. Basically, all you need to do is set a Root User password so please navigate to those instructions in the aforementioned link. If you need further assistance, please contact its@manhattan.edu.
USA Today Article
Apple has released an update that fixes this vulnerability. Please update your Mac ASAP.
Here is the information regarding the update.
A security hole was recently discovered in the latest version of Mac OS X High Sierra which allows for anyone to access your computer without a password. We have provided a link to a USA Today article below, but there are many articles on the web reporting this issue. While Apple is working on a fix via update, you should take immediate action to fix the issue by following the instructions here. Basically, all you need to do is set a Root User password so please navigate to those instructions in the aforementioned link. If you need further assistance, please contact its@manhattan.edu.
USA Today Article
Tuesday, November 28, 2017
Reminder: Transition to Google Drive File Stream
Google Drive Sync ends support on December 11, 2017.
Solution:
Install Google Drive Stream. At the conclusion of the installation, you will get a pop up asking whether you want to replace Google Drive Sync with Drive Stream or whether you want to use both. It is recommended that you select "Yes" indicating that you wish to replace.
What about the current Drive application? Before installing File Stream, Google recommends removing the current Drive folder. For ease of use, we think it's best to uninstall the current Drive client.
Uninstall Drive and install File Stream
1. Uninstall the previous Google Drive app or Backup and Sync if it is present on your computer. To uninstall, navigate to the Windows icon in the bottom left corner of the screen and search for "Control Panel" and proceed to open it. You should be greeted with this window:
 Once you click on "Program and Features", you will be shown a list of programs that are installed on your computer. Navigate to the Google Drive app that you previously installed on your PC and select it. You will then see appear the option to uninstall that program. Proceed with the uninstall to completely remove the program from your PC.
Once you click on "Program and Features", you will be shown a list of programs that are installed on your computer. Navigate to the Google Drive app that you previously installed on your PC and select it. You will then see appear the option to uninstall that program. Proceed with the uninstall to completely remove the program from your PC.
2. Delete Google Drive Sync folder from your computer. It is a local folder only now and no longer syncs.
3. Install Drive File Stream. You can find it here. Depending on preferences of the User, it can be a good idea to create shortcuts on the desktop and in the Favorites or Quick Access areas of Windows and MacOS. We also recommend removing any shortcuts to the previous Google Drive folder to avoid confusion.
Also, the Drive File Stream icon in the Windows task bar will be grey, that should be the only Google Drive icon found in the task bar. If you see the older Google Drive Sync colored icon still on your computer go back to step 2 and delete old Google Drive Sync folder.

About:
Drive File Stream is a new way to access all of your Google Drive files directly from your Mac or PC, without using up all your disk space. Unlike traditional file sync tools, Drive File Stream doesn’t require you to download your files first in order to access them from your computer. Instead, when you need to view or edit a file, it automatically streams from the cloud, on-demand. With Drive File Stream, your team will spend less time waiting for files to sync, no time worrying about disk space, and more time being productive.
With Drive File Stream, you can:
- Quickly see all your Google Drive files in Finder/Explorer (including Team Drives).
- Browse and organize Google Drive files without downloading all of them to your computer.
- Choose which files or folders you'd like to make available offline.
- Open files in common apps like Microsoft Office and Adobe Photoshop.
Environment
Windows
MacOSX
Google Drive
How do I get started?
Visit the Drive Help Center to install Drive File Stream and get started.
Manhattan College ITS receives Cloud Leadership Award
 The Manhattan College ITS (Information Technology Services) Office has been recognized for its leadership in deploying Hybrid IaaS/PaaS (Infrastructure/Platform as a Service) Cloud solutions by E&I Cooperative Services (E&I) in their inaugural Cloud Leadership Awards ceremony.
The Manhattan College ITS (Information Technology Services) Office has been recognized for its leadership in deploying Hybrid IaaS/PaaS (Infrastructure/Platform as a Service) Cloud solutions by E&I Cooperative Services (E&I) in their inaugural Cloud Leadership Awards ceremony. Winners were awarded during the EDUCAUSE 2017 Annual Conference reception held on November 2, 2017 in Philadelphia, P.A. The Cloud Leadership Awards honor the achievements of higher education institutions that have benefited students, teachers, administrators, and staff by using cloud solutions.
Monday, November 27, 2017
COMPLETE - Horan Hall - Brief Network Outage 11/29 at 10am
UPDATE: As of about 10:45am yesterday, the generator test was completed. If you have any questions, please contact ITS at its@manhattan.edu or x-7973.
Physical Plant will be conducting a generator test in Horan Hall Wednesday, November 29th at approximately 10am.
There will be two brief outages, one while switching to generator power, the other while switching back to main power.
This will not affect the rest of campus.
Physical Plant will be conducting a generator test in Horan Hall Wednesday, November 29th at approximately 10am.
There will be two brief outages, one while switching to generator power, the other while switching back to main power.
This will not affect the rest of campus.
LabSeat: Find an Open Computer on Campus
Have you ever encountered a situation when you needed to use a lab computer, but you arrived and all of the computers were already in use? Looking for a quiet corner to study?
Direct Link:
https://go.manhattan.edu/labseat
Via the ITS website: https://inside.manhattan.edu/offices/its/computer-labs.php
Well, thanks to a new web application called LabSeat that was installed on our lab computers earlier this year, you can check computer availability in real time before you leave for the lab. This will be especially useful during busier times such as midterms and finals week as you can choose where to study by how many computers are available.
Access the LabSeat application to view computer availability via any of the methods below:
https://go.manhattan.edu/labseat
- Take a look at the list of labs and click on the lab you would like to view
Via the college's Quicklinks on the insidemanhattan.edu website or the Glance MC App, using any of the following search terms: computer, lab,LabSeat, etc. (Note Glance MC IOS users can save the link to their app Favorites)
Via the ITS website: https://inside.manhattan.edu/offices/its/computer-labs.php
Click on the arrow at the end of the room and you will see:
- A map of the Computer Lab
- Hours computer lab is open
- Classes scheduled in each classroom/open lab
For more information click on KBA titled: LabSeat: Find an Open Computer on Campus
COMPLETE - Licensing Issue: Aspentech HYSYS is Down
Update:
Licensing issue has been fixed as of 2:45 PM. Aspentech products should be fully functional.
Original Post:
ITS is aware of a licensing issue currently preventing AspenTech HYSYS from functioning.
The license expired this past Friday at midnight. We have been working with their support team since then to resolve the problem. They appear to have been closed for most of the holiday weekend.
We will update this post as soon as we have any more information.
Licensing issue has been fixed as of 2:45 PM. Aspentech products should be fully functional.
Original Post:
ITS is aware of a licensing issue currently preventing AspenTech HYSYS from functioning.
The license expired this past Friday at midnight. We have been working with their support team since then to resolve the problem. They appear to have been closed for most of the holiday weekend.
We will update this post as soon as we have any more information.
Monday, November 20, 2017
New Dorm Wifi Feedback Form!
ITS is making strides to improve the wireless networks in the dorms across campus. We have made it easier to put in wifi complaints with a new Dorm Wireless Feedback Form!
There are several ways you can access the form to make your wifi complaints:
There are several ways you can access the form to make your wifi complaints:
- You can visit the following link to access the form: https://go.manhattan.edu/dormwifi
- Access the form from the GlanceMC app, found under the Featured Links section
ITS Customer Satisfaction Survey
Please take a moment to fill out the semesterly ITS Customer Satisfaction Survey. Please try to think only of your experience with ITS for the Fall 2017 semester. Here is a link to the survey.
Thank you for your feedback.
Sunday, November 19, 2017
Reminder: Transition to Google File Stream
Please note Google Drive Sync ends support on December 11, 2017.
This change will require you to take action and transition to Google File Stream.
Visit the Drive Help Center to install Drive File Stream and get started.
Refer to previous blog posts for more information:
Google Drive Just Got Easier for You and Your Team
If you need assistance with the transition please contact ITS.
Call: 718-862-7973
Email: its@manhattan.edu
Email: its@manhattan.edu
Friday, November 17, 2017
Scheduled Maintenance Downtime - Banner & Self-Service
Information
Technology Services will be performing scheduled maintenance on our Administrative systems. This scheduled maintenance will require Banner and Self-Service to be off line on November 18, 2017 between 9:00pm - 1:00am. (4 hours).
Thank
you for your patience during this time.
Information
Technology Services
Labels:
Banner 9,
ITS,
maintenance,
SSB
Thursday, November 16, 2017
UPDATE: 310pm RESOLVED --- Campus Wide Issue Affecting Network and DHCP
The issue was resolved at approximately 2:45.
We do not expect it to reoccur.
----
This is a known issue. We are working on resolving this issue right now. In the meantime there may be sporadic internet outages.
We will update once the issue is resolved.
We do not expect it to reoccur.
----
This is a known issue. We are working on resolving this issue right now. In the meantime there may be sporadic internet outages.
We will update once the issue is resolved.
Convert text to all CAPS and more in Google Docs
Capitalizing a large portion of text or an especially long title can be a pain. Doing the opposite—converting capital letters to lowercase—is equally a waste of time. With this launch, we’re making those tasks quick and easy in Google Docs on the web.
Starting today, simply choose “Capitalization” from the Format menu in Docs, and select one of the following:
It’s that easy. Like other recent launches in Docs, this feature allows you to spend less time formatting and more time on the things that matter, like strategizing, collaborating, and developing new ideas.
Partially reposted from: https://gsuiteupdates.googleblog.com/2017/03/convert-text-to-all-caps-and-more-in.html
Starting today, simply choose “Capitalization” from the Format menu in Docs, and select one of the following:
- lowercase, to make all the letters in your selection lowercase.
- UPPERCASE, to capitalize all the letters in your selection.
- Title Case, to capitalize the first letter of each word in your selection.
It’s that easy. Like other recent launches in Docs, this feature allows you to spend less time formatting and more time on the things that matter, like strategizing, collaborating, and developing new ideas.
Partially reposted from: https://gsuiteupdates.googleblog.com/2017/03/convert-text-to-all-caps-and-more-in.html
Wednesday, November 15, 2017
Jamboard Update: Create and Edit Objects in Jams on Your Mobile Phone
Building off of the recent improvements to the Jamboard app for your mobile phone, the latest Jamboard release allows you to do even more on the go with your phone. We’re also making it easier to move content between frames on your Jamboard device.
Create and edit objects in jams on your mobile phone
Creating and collaborating on jams just got even easier. You can now use the Jamboard app on your Android and iOS phones to:
In addition, for quicker editing within jams, you can now move objects to other frames easily via the frame bar at the top of your Jamboard device screen.
For a full list of new features and improvements from this month’s release, check out the What’s New in Jamboard page in the Help Center.
Create and edit objects in jams on your mobile phone
Creating and collaborating on jams just got even easier. You can now use the Jamboard app on your Android and iOS phones to:
- Create jams
- Move/scale/rotate objects
- Move objects to adjacent frames
- Delete and duplicate objects
- Undo/redo changes
- Edit sticky notes
- Zoom in and out, and pan
- And more...
In addition, for quicker editing within jams, you can now move objects to other frames easily via the frame bar at the top of your Jamboard device screen.
For a full list of new features and improvements from this month’s release, check out the What’s New in Jamboard page in the Help Center.
Tuesday, November 14, 2017
Shop Safe Online, Even on Black Friday!
In 2016, for the first time ever, shoppers bought more online than in stores. All Internet-connected devices are vulnerable, especially when being used for purchases. You need to be aware of ways to protect yourself as you shop online.
The holiday season is the perfect time for cybercriminals to take advantage of unsuspecting online shoppers. When you go to the grocery store or local shop, it's habit to grab your reusable bags, lock the car, and make sure you've safely put away your credit card or cash before heading home with the day's purchases. Similar precautions need to be taken when you're shopping online from the comfort of your own home. If you make these simple precautions regular online shopping habits, you'll be protecting your purchases and personal information.
The National Cyber Security Alliance recommends following these basic steps so you'll be ready to cybershop safely and securely.
- Lock down your login. One of the most critical things you can do in preparation for the online shopping season is to fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like e-mail, banking, and social media.
- Keep clean machines. Before searching for that perfect gift, be sure that all web-connected devices—including PCs, mobile phones, smartphones, and tablets—are free from malware and infections by running only the most current versions of software and apps.
- Shop reliable websites online. Use the sites of retailers you trust. If it sounds too good to be true, it probably is!
- Conduct research. When using a new website for your holiday purchases, read reviews and see if other customers have had a positive or negative experience with the site.
- Personal information is like money: value it and protect it. When making a purchase online, be alert to the kinds of information being collected to complete the transaction. Make sure you think it is necessary for the vendor to request that information. Remember that you only need to fill out required fields at checkout.
- Get savvy about Wi-Fi hotspots. If you are out and about, limit the type of business you conduct over open public Wi-Fi connections, including logging in to key accounts, such as e-mail and banking. Adjust the security settings on your device to limit who can access your phone. If you must use open Wi-Fi connections, connect to a virtual private network (VPN) first.
- Check the address bar. Look for the green lock icon and https:// in the URL before using your credit card online.

Monday, November 13, 2017
How to Get the New Google Calendar on the Web Right Now
In follow up to this previous blog post about the new Google Calendar for Web, follow these instructions to begin using the New Google Calendar for Web:
Navigate to the Google Calendar App on your Apps Launcher:
Look for a button near the top right corner (between Agenda and More buttons) that says Use New Calendar.
After switching you can customize the appearance by clicking the settings cog in the upper right portion of the screen. To revert to the old design altogether you may select the Back to Classic Calendar.
Partially reposted from: https://www.cnet.com/how-to/how-to-get-the-new-google-calendar-on-the-web-right-now/
Navigate to the Google Calendar App on your Apps Launcher:
Look for a button near the top right corner (between Agenda and More buttons) that says Use New Calendar.
If you already have the Calendar open, refresh the page to get the button to appear.
Click on the Upgrade now button:
Click "Learn more about the new design" to get an overview of the new features in Calendar:
The new Google Calendar is cleaner, has more white space and is easier to read.
Partially reposted from: https://www.cnet.com/how-to/how-to-get-the-new-google-calendar-on-the-web-right-now/
Reminder: Transition to Google File Stream
Please note Google Drive Sync ends support on December 11, 2017.
This change will require you to take action and transition to Google File Stream.
Visit the Drive Help Center to install Drive File Stream and get started.
Refer to previous blog posts for more information:
Google Drive File Stream
Google Drive Just Got Easier for You and Your Team
If you need assistance with the transition please contact ITS.
Call: 718-862-7973
Email: its@manhattan.edu
This change will require you to take action and transition to Google File Stream.
Visit the Drive Help Center to install Drive File Stream and get started.
Refer to previous blog posts for more information:
Google Drive File Stream
Google Drive Just Got Easier for You and Your Team
If you need assistance with the transition please contact ITS.
Call: 718-862-7973
Email: its@manhattan.edu
Saturday, November 11, 2017
Planned Banner Upgrades
Information
Technology Services will be performing a planned point release upgrade to the Banner
administrative system. This scheduled maintenance will require the
server to be off line on November 11 between 9:00pm - 10:00pm.
Thank
you for your patience during this short outage.
Information
Technology Services
Labels:
Banner 9,
ITS,
maintenance,
Self-Service,
SSB
Wednesday, November 8, 2017
Protecting Yourself from Phishing Strategies
Criminals who “phish” use different strategies to obtain your sensitive information. Many times phishing is associated with email but it is any strategy used where the goal is to “phish” sensitive information from you.
You may not realize it, but you are a phishing target at school, at work, and at home. Ultimately, you are the most effective way to detect and stop phishing scams. When viewing email messages, texts, or social media posts, look for the following indicators to prevent stolen passwords, personal data, or private information.Protecting Yourself
- Keep your Browser Updated. Phishers are exploiting a flaw in the web browsers “punycode.” “Punycode” is in charge of translating foreign domain names into English. This means criminals can register a domain name that, even after close visual inspection, appears normal.
- Misspelling web addresses. Phishers can use a look-alike domain name such as “Goggle.com” hoping that you misspelled “Google.com.” Use bookmarks for trusted websites to avoid manually typing web addresses.
- Be suspicious of websites not using a certificate. A website using a digital certificate indicates that they are the rightful owner of the website. Certified websites will have an image of a lock and in Chrome the word Secure in green letters directly on the address bar. However, just because a website has a digital certificate doesn't necessarily mean that it is safe but it is a good indicator.
ex. Safari Digital Certificate
ex. Chrome Digital Certificate
Subscribe to:
Posts (Atom)